|
25.01.2023 20:06:00
|
Reduce Security Compliance Program Complexity by Using a Single Control Framework, Says Info-Tech Research Group
An effective security compliance program reduces costs and efforts and improves information security practices.
TORONTO, Jan. 25, 2023 /PRNewswire/ - In today's security landscape, most organizations spend a large portion of their security budget on compliance-related activities. Despite this growing investment in compliance, only a small percentage of organizations believe that government regulations help improve cybersecurity. To help security leaders reduce compliance complexity, costs, and efforts, global IT research and advisory firm Info-Tech Research Group has released its new Build a Security Compliance Program blueprint.
According to the firm's research, the cost of complying with cybersecurity and data protection requirements has risen to the point where most organizations see it as a barrier to entering new markets. However, research in the report also shows that the cost of non-compliance can be up to three times greater than the cost of compliance.
"These days, it is hard to find a security leader who welcomes new regulations," says Kate Wood, security and privacy research practice lead at Info-Tech Research Group. "The majority of organizations already manage five or more compliance obligations, and most allocate at least 25% of their security budget to compliance activities. Yet, for all the good intentions behind these regulations, very few security professionals believe that government rules improve organizational cybersecurity. At this point, compliance obligations are inevitable, but it is possible to manage them without breaking the bank."
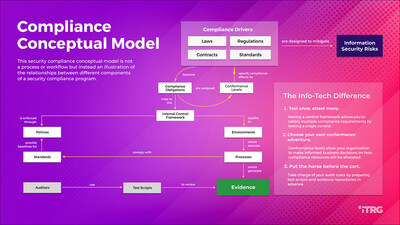
Info-Tech's blueprint highlights the benefits of having an effective security compliance program. For example, for IT, a security compliance program reduces the complexity within the control environment by using a single framework to align multiple compliance regimes, decreases costs and efforts related to managing IT audits through planning and preparation, and improves information security practices through self-assessments.
For the business side, an effective security compliance program provides senior management with a structured framework for making business decisions on allocating costs and efforts related to cybersecurity and data protection compliance obligations. It also helps to reduce compliance risk and enables visibility into compliance status.
The firm's blueprint outlines a five-phase holistic approach to building an effective security compliance program:
Phase 1 – Establish- Review and adopt an information security control framework.
- Understand and establish roles and responsibilities for security compliance management.
- Identify and scope operational environments for applicable compliance obligations.
- Identify the security compliance obligations that apply to the organization.
- Document obligations and obtain direction from management on conformance levels.
- Map compliance obligation requirements into the control framework.
- Update security policies and other control design documents to reflect required controls.
- Align compliance obligations with an information security strategy.
- Develop a process to attest to control design.
- Create scripts to test controls.
- Conduct self-assessments on required controls.
- Understand how to manage audits.
- Track the status of compliance obligations.
- Manage exceptions to compliance requirements.
- Report on the compliance management program to senior stakeholders.
The blueprint states that compliance risk is not the same as security risk, as it is primarily concerned with the potential legal consequences of non-compliance, such as regulatory fines or contractual penalties. However, since most cybersecurity and data protection laws and regulations are designed to address security risks, non-compliance may also leave an organization open to security risks.
For more information and insights on the research methodology, download the complete Build a Security Compliance Program blueprint.
To learn more about Info-Tech Research Group, visit infotech.com and connect via LinkedIn and Twitter.
About Info-Tech Research GroupInfo-Tech Research Group is one of the world's leading information technology research and advisory firms, proudly serving over 30,000 IT professionals. The company produces unbiased and highly relevant research to help CIOs and IT leaders make strategic, timely, and well-informed decisions. For 25 years, Info-Tech has partnered closely with IT teams to provide them with everything they need, from actionable tools to analyst guidance, ensuring they deliver measurable results for their organizations.
Media professionals can register for unrestricted access to research across IT, HR, and software and over 200 IT and Industry analysts through the ITRG Media Insiders Program. To gain access, contact pr@infotech.com.
![]() View original content to download multimedia:https://www.prnewswire.com/news-releases/reduce-security-compliance-program-complexity-by-using-a-single-control-framework-says-info-tech-research-group-301730795.html
View original content to download multimedia:https://www.prnewswire.com/news-releases/reduce-security-compliance-program-complexity-by-using-a-single-control-framework-says-info-tech-research-group-301730795.html
SOURCE Info-Tech Research Group
 Der finanzen.at Ratgeber für Aktien!
Der finanzen.at Ratgeber für Aktien!
Wenn Sie mehr über das Thema Aktien erfahren wollen, finden Sie in unserem Ratgeber viele interessante Artikel dazu!
Jetzt informieren!